Advanced Security and Row-Level Permissions in Power BI with Microsoft Purview

Why RLS and Data Governance Matter More Than Ever
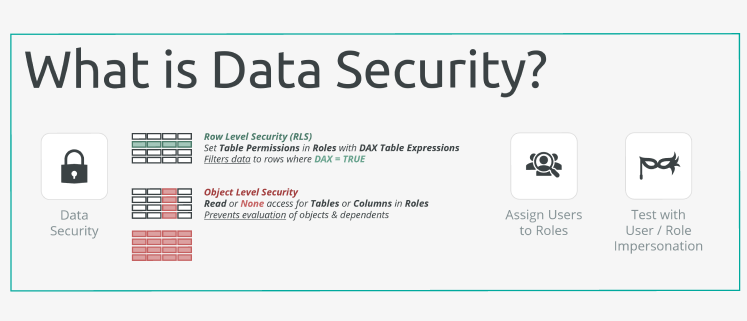
Understanding Row-Level Security (RLS) in Power BI
Row-Level Security (RLS) in Power BI is a mechanism that filters data based on the identity of the logged-in user. Instead of creating multiple reports for different departments or user groups, RLS enables dynamic filtering—so a single report can serve multiple audiences with appropriate data visibility.
How RLS Works in Power BI
- Role Definition: In Power BI Desktop, you create roles and assign DAX filters that determine which rows of data users in those roles can access.
- Publishing to Power BI Service: Once published, you map users or security groups to those roles in the Power BI Service.
- Dynamic Filtering: With dynamic RLS, the filter uses DAX functions like USERNAME() or USERPRINCIPALNAME() to restrict data based on the logged-in user.
Example DAX Filter:
[Region] = USERPRINCIPALNAME()
This ensures that users see only the rows where their name matches the Region field.
Best Practices for Implementing RLS in Power BI Desktop
Enforcing RLS correctly requires a clear understanding of the data model and how filters interact across tables. Here are some best practices to follow:
- Use Star Schema for Effective Filtering
A star schema with fact and dimension tables simplifies the implementation of RLS. Apply filters to dimension tables and allow relationships to handle the filtering on fact tables. - Validate Role Filters Thoroughly
Always test role filters within Power BI Desktop before publishing. Use the “View As Role” feature to simulate what users in each role will see. - Avoid Ambiguous Relationships
Avoid bi-directional relationships unless necessary. These can cause unintended data exposure when RLS filters propagate in both directions. - Use Dynamic RLS Cautiously
Dynamic RLS scales better than static role assignments, but it requires accurate mapping tables and careful DAX configuration to avoid loopholes. - Secure All Layers of Access
Remember that RLS is only enforced within the Power BI ecosystem. Exporting data or sharing it outside of Power BI may bypass RLS protections.
Integrating Microsoft Purview for Centralized Data Governance
Microsoft Purview is a unified data governance solution that allows you to discover, classify, and manage data across your organization. When paired with Power BI, it provides a broader layer of security and compliance, especially critical for large enterprises managing multiple data sources and user roles.
Key Capabilities of Microsoft Purview in Power BI Context
- Data Cataloging: Automatically scans Power BI datasets and maps them in a searchable catalog.
- Data Lineage Tracking: Visualize end-to-end data flows—from source systems to Power BI dashboards.
- Sensitivity Label Inheritance: Sensitivity labels from Microsoft Information Protection can be inherited in Power BI reports and dashboards.
- Access Insights: Monitor who is accessing what data and when—helping ensure RLS policies are effective and followed.
Using Purview to Enhance Power BI RLS Enforcement
1. Classify and Label Sensitive Data
Before applying RLS, use Microsoft Purview to classify your data assets. Identify sensitive information (e.g., customer PII, financial data) and apply labels such as “Confidential” or “Internal Only.”
Once labeled, these classifications can propagate to Power BI reports, ensuring RLS roles align with your data governance policies.
2. Define Data Access Policies Centrally
Purview allows centralized management of access policies based on roles, geographies, or compliance requirements. These policies can then be enforced in Power BI through integration with Azure Active Directory and Microsoft Defender for Cloud Apps.
This centralization reduces the risk of inconsistent policy application across different datasets and workspaces.
3. Monitor Compliance and Usage Patterns
With Purview’s audit capabilities, you can detect anomalies—such as unauthorized access to restricted data—even if RLS is applied. This allows real-time policy adjustments to tighten data security.
Advanced Use Cases: Combining RLS with Sensitivity Labels
RLS works at the data level, but what if you want to prevent actions like sharing, exporting, or copying specific content based on its sensitivity?
This is where Microsoft Information Protection (MIP), integrated with Purview, comes in. Sensitivity labels can:
- Restrict downloading or printing of sensitive reports.
- Enforce encryption when reports are shared via email.
- Trigger DLP (Data Loss Prevention) policies if someone tries to export restricted data.
These controls complement RLS and ensure end-to-end protection of your data—whether in reports, dashboards, or shared files.
Real-World Example: Regional Sales Reporting
Imagine a multinational company using Power BI for global sales analysis. Each regional manager should see only their own region’s data. Here’s how RLS and Purview work together:
- RLS Setup in Power BI: Roles are created for each region with DAX filters based on Region ID.
- User Mapping: Users are assigned to roles using Active Directory groups.
- Purview Classification: Sales data is tagged as “Confidential – Financial.”
- Sensitivity Labels: Applied to Power BI reports to restrict export/sharing actions.
- Monitoring: Purview tracks access logs and alerts on abnormal user behavior (e.g., a manager accessing another region’s data).
This combined approach ensures granular access and enterprise-grade control across every layer of the data lifecycle.
Common Pitfalls to Avoid
Even with robust tools, security implementation can go wrong. Here are frequent mistakes:
- Forgetting to assign users to roles after publishing the report.
- Using RLS only on fact tables, causing filters to break due to relationship gaps.
- Assuming RLS applies to Excel-connected datasets, which it doesn’t unless through Power BI Service.
- Mislabeling sensitive data in Purview, resulting in incorrect access assumptions.
To avoid these, always involve both BI developers and data governance teams during implementation.
Conclusion: RLS + Purview = Secure, Scalable, Compliant BI
Power BI’s Row-Level Security is a powerful tool for managing data visibility, but it shines brightest when supported by a centralized data governance platform like Microsoft Purview. Together, they help businesses enforce access controls, apply regulatory compliance, and build user trust through responsible data handling.
Whether you’re building a small departmental dashboard or a global data model, understanding how RLS filters rows—and how Purview monitors and governs those access rules—is critical to creating secure, scalable, and compliant business intelligence solutions.
Is your organization ready to take Power BI security to the next level with Microsoft Purview integration?
At Code Creators, we help organizations elevate their data strategy through expert Power BI consulting and governance-focused implementations. Whether you’re building secure dashboards with Row-Level Security or integrating Microsoft Purview for enterprise-grade compliance, working with a seasoned Power BI consultant ensures that your analytics environment is both powerful and protected. Let us help you unlock insights while maintaining control, security, and trust in every report you build.
Sherry Rajani, is a tie-loathing adventurer and troublemaker who believes in turning ideas into reality. Even though his experience is primarily in Microsoft Cloud and On-Premise Solutions, Sherry has also lead teams building Custom ERPs, Mobile Applications, Data Management and other solutions.
After working in the Toronto Technology Industry for a while, Sherry started his own Technology Consulting Firm, Code Creators Inc., specializing in the Office 365 Stack ranging from SharePoint Online, the Power Platform, PowerBI and Microsoft Teams.



